Author
Sanaddhya Kaushik
So, how did this breach occur? The attackers utilized a combination of techniques, including "vishing" (voice phishing) and "social engineering," which involves manipulating individuals into revealing sensitive information. In this particular case, the hackers reportedly exploited publicly available information on LinkedIn to impersonate an MGM employee. They skillfully deceived someone within MGM's IT help desk, ultimately coaxing them into divulging access credentials. Now, identifying the culprits behind this incident is a complex task, as two distinct yet interconnected groups have claimed responsibility. Firstly, there's " Scattered Spider," a group believed to comprise hackers from Europe and the United States, primarily in their teens and twenties, known for their prowess in social engineering. A representative claiming to be from Scattered Spider revealed to the Financial Times that their initial plan was to manipulate MGM's slot machines, reminiscent of the plot in "Ocean's Thirteen," although they asserted they'd never actually watched the film. When this scheme failed, they resorted to holding stolen data for ransom instead. Scattered Spider has also allegedly targeted Caesars Entertainment, which ended up paying a hefty $15 million in ransom. On the other hand, there's " Alphv/Black Cat," an entity running a ransomware-as-a-service business, providing malware to other hackers. This group was responsible for nearly 12% of cyberattacks in the first four months of 2022 and recently made headlines by posting 2.5 terabytes of stolen data from semiconductor maker Seiko. In a statement, Alphv/Black Cat claimed to be the true perpetrator of the MGM cyberattack (though not the attack on Caesars) and denied involvement in the slot machine plot. The MGM cyberattack is a stark reminder of the evolving tactics used by cybercriminals and the importance of robust cybersecurity measures to safeguard sensitive information and systems.
Black Cat Ransomware Vulnerable drivers
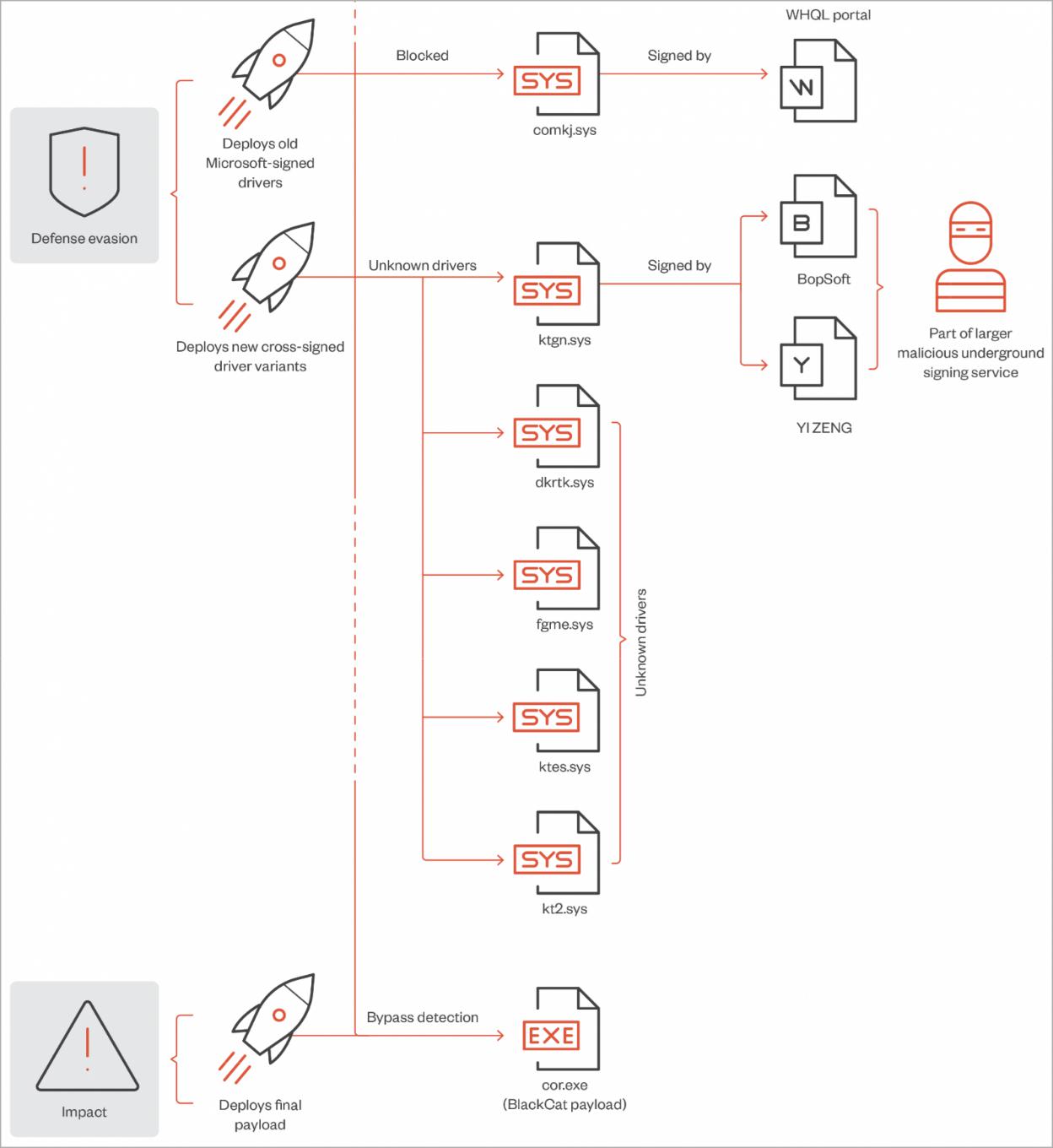
How this process work
1. Activate driver
2. Deactivate the driver after the user mode client fnishes its operation
3. Kill any user-mode process
4. Delete specifc fle paths
5. Force-delete a fle by freeing its handles and terminating running processes using it 6. Copy fles
7. Force-copy fles using a similar mechanism to force-delete
8. Register Process/Thread Notifcation callbacks
9. Unregister Process/Thread Notifcation callbacks
10. Reboot the system by calling the 'HalReturnToFirmware' API
Preventive Measures
Continuous Penetration Testing:
● Implement continuous penetration testing as an integral part of your security strategy.
● Regularly assess your systems and networks for vulnerabilities and weaknesses.
● Use penetration testing to proactively identify and address potential security flaws before they can be exploited by threat actors.
Threat Intelligence:
● Stay updated on the latest threat actors and tactics. ● Regularly update threat intelligence to defend against known groups like Scattered Spider. ● Ensure asset and VM management deploy new CVEs and scripts based on accurate vulnerability risk prioritization.
Detection and Remediation with Custom Logic:
● Invest in advanced threat detection and prevention systems.
● Develop the capability to create custom vulnerability detection and remediation scripts, especially for zero-day exploits.
Zero-Trust Architecture:
● Implement a zero-trust security model.
● Assume that no one, even within your network, can be trusted without verification.
● Focus on containing lateral movement after an initial breach using a strict Zero Trust Network Access (ZTNA) strategy.
Incident Response Plan:
● Review and update your incident response plan.
● Ensure it accounts for Advanced Persistent Threats (APTs) and sophisticated attackers.
● Regularly test the plan to optimize coordination between security and IT teams and reduce Mean Time to Respond (MTTR).
Employee Training:
● Continuously educate and train employees on cybersecurity best practices.
● Specifically, focus on recognizing and reporting phishing attempts.
Red Team Testing:
● Conduct regular red teaming exercises.
● Simulate real-world attacks to identify vulnerabilities before malicious actors do.
